If your organization uses Okta to manage your employees access to tools and services, you can take advantage of Okta’s “Provisioning” feature to automatically maintain traveller profiles in Umbrella Faces for your users.
The integration between Okta and Contentful that enables this provisioning to occur is built around an industry-standard protocol known as SCIM (System for Cross-domain Identity Management). To learn more about how Okta works with SCIM, please see this article.
Features
The following provisioning features are currently supported by Umbrella Faces
| Feature | Description |
|---|---|
| Create users | Users in Okta that are assigned to the Umbrella Faces application are automatically added as travellers to Umbrella Faces. |
| Update user attributes | Updating an user in Okta will also update the linked attributes in Umbrella Faces |
| Deactivate users | Unassigning Users from Umbrella Faces in Okta will cause the associated traveller profile to be removed from Umbrella Faces. Please note: Faces does not recognize an "active" state on a profile. Hence if a profile is set to inactive it will be deleted along with all associated data |
Requirements
In order to use SCIM provisioning you will need to be an existing Faces customer and in possession of an administrative account which is allowed to manage traveler profiles. The administrative account can either be a Company- or Agency-Administrator
Please note that SCIM can be enabled in a self-service fashion, but will incur an additional charge once activated.
How to configure
Enable provisioning functionality
In Umbrella Faces
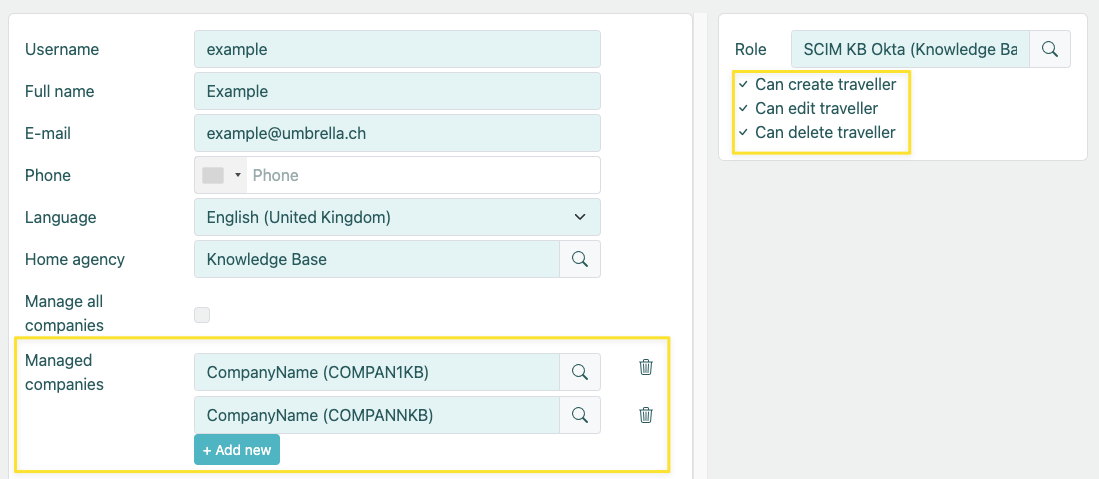
While it is possible to use any administrator, we do recommend creating a dedicated user account with access limited to the scope of the integration. (e.g. Company Administrator account with "Can Create / Edit / Delete Traveller" rights)
In Okta
Log in to your Okta admin portal and complete the following steps:
- Under the Applications tab, navigate to the Umbrella Faces application.
Click on the General tab in the application.
Under the "App Settings" section enter the Faces Base URL in the field.
This should be the address of where you login to Faces minus the "/login" portion. For example if you usually login at https://tenzing.umbrella.ch/faces/login you'll have to enter https://tenzing.umbrella.ch/faces
- Click on the “Provisioning” tab in the application. Under the “Settings” panel on the left side, click the “Integration” link.
- Click the “Configure API Integration” button.
- Check "Enable API integration" checkbox
- Click the "Authenticate with Umbrella Faces" Button
- Okta will open a pop-up window, where you'll be able to sign-in to Umbrella Faces and authorize the connection
- Once you've authorized the access, save and go back to the provisioning tab
Under the “Settings” panel on the left side, click “To App” under the Settings panel on the left.
Click the "Edit" button at the top right. Check the “Enable” box next to “Create Users”, "Update User Attributes" and "Deactivate Users"
You should now be able to assign your Okta users to the Umbrella Faces application as needed, with their profiles automatically showing up as traveller profiles.
Configure Okta to Umbrella Faces Mappings
To configure additional field mappings between Okta and Umbrella Faces perform the following steps:
- Under the Applications tab, navigate to the Umbrella Faces application.
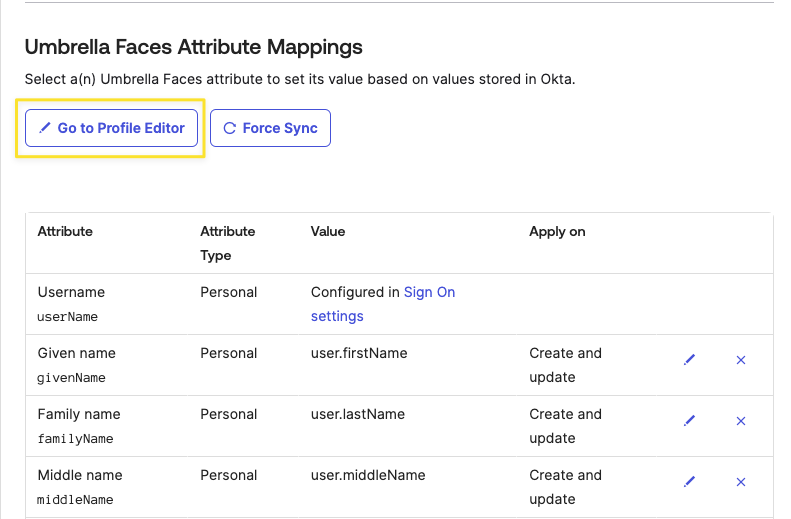
- Click on the “Provisioning” tab in the application. Under the "To App" panel on the left side scroll to the bottom and select "Go to Profile Editor"
Within the profile editor you'll be able to change the predefined mappings as well as add additional mappings for custom data fields within Faces.
Known Issues / Troubleshooting
| Known Issue / Limitation | Solution |
|---|---|
| Faces does not support deactivation of travellers | Whenever a profile is set to inactive, we will delete it on our end. |
| Supported Data fields | The following standard SCIM fields are supported:
Additionally, we support custom attributes as defined in "Attribute Definitions" below. Please do not hesitate to reach out to us should you wish for further data fields to be made available |
Attribute Definitions
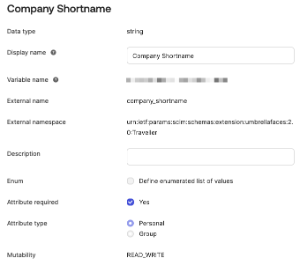
Company Shortname
By default this attribute is mapped to 'EXAMPLE', you'll want to update this to reflect an actual company shortname, either statically or via a function or other data field.
At the very least, Umbrella Faces will require you to setup a mapping for "company_shortname", which is responsible for mapping the travellers to the correct company within Faces.
| External name | company_shortname |
|---|---|
| External namespace | urn:ietf:params:scim:schemas:extension:umbrellafaces:2.0:Traveller |
| Example |
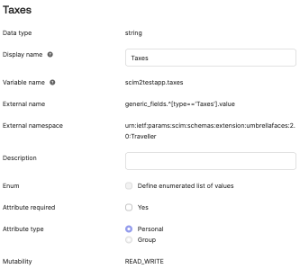
Generic Field Value
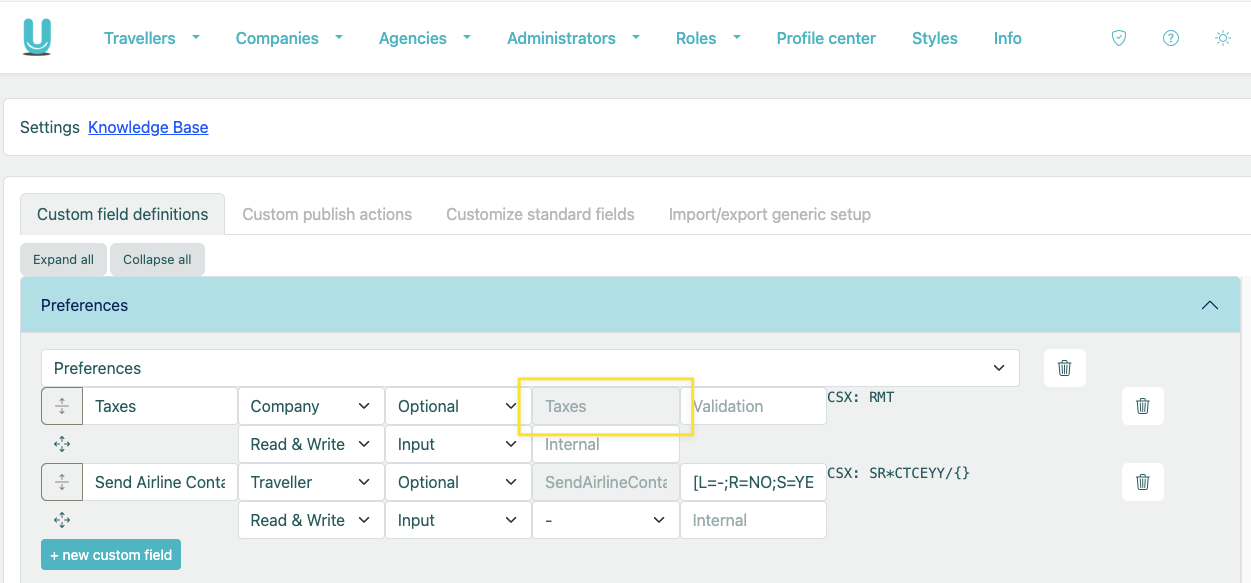
To setup a mapping of a generic field value, first find the field name from the Umbrella Faces administrative UI
Then setup the attribute in Okta as follows and add a mapping
| External name | generic_fields.^[type=='UmbrellaFacesFieldName'].value |
|---|---|
| External namespace | urn:ietf:params:scim:schemas:extension:umbrellafaces:2.0:Traveller |
| Example |